.svg?table=block&id=b23a9dca-d6a4-4f43-b2a3-9ae1b7dbe031&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
 Series A Pitch
Series A Pitch
.svg?table=block&id=b23a9dca-d6a4-4f43-b2a3-9ae1b7dbe031&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)

Simon He -- simon@m.convequity.com
Jordan Lambert -- jordan@m.convequity.com
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
Access Control -- for the third straight quarter it's the reason for the largest exploits
Exchanges can still mask holes in their balance sheets; regulators now demand real-time on-chain proof collateral exists.
Bridges and DeFi apps often launch with single-sig keys; one compromised key can drain every user wallet.
Audits stop at launch; configs drift, keys rotate, new code ships un-reviewed--fresh attack surface every week.
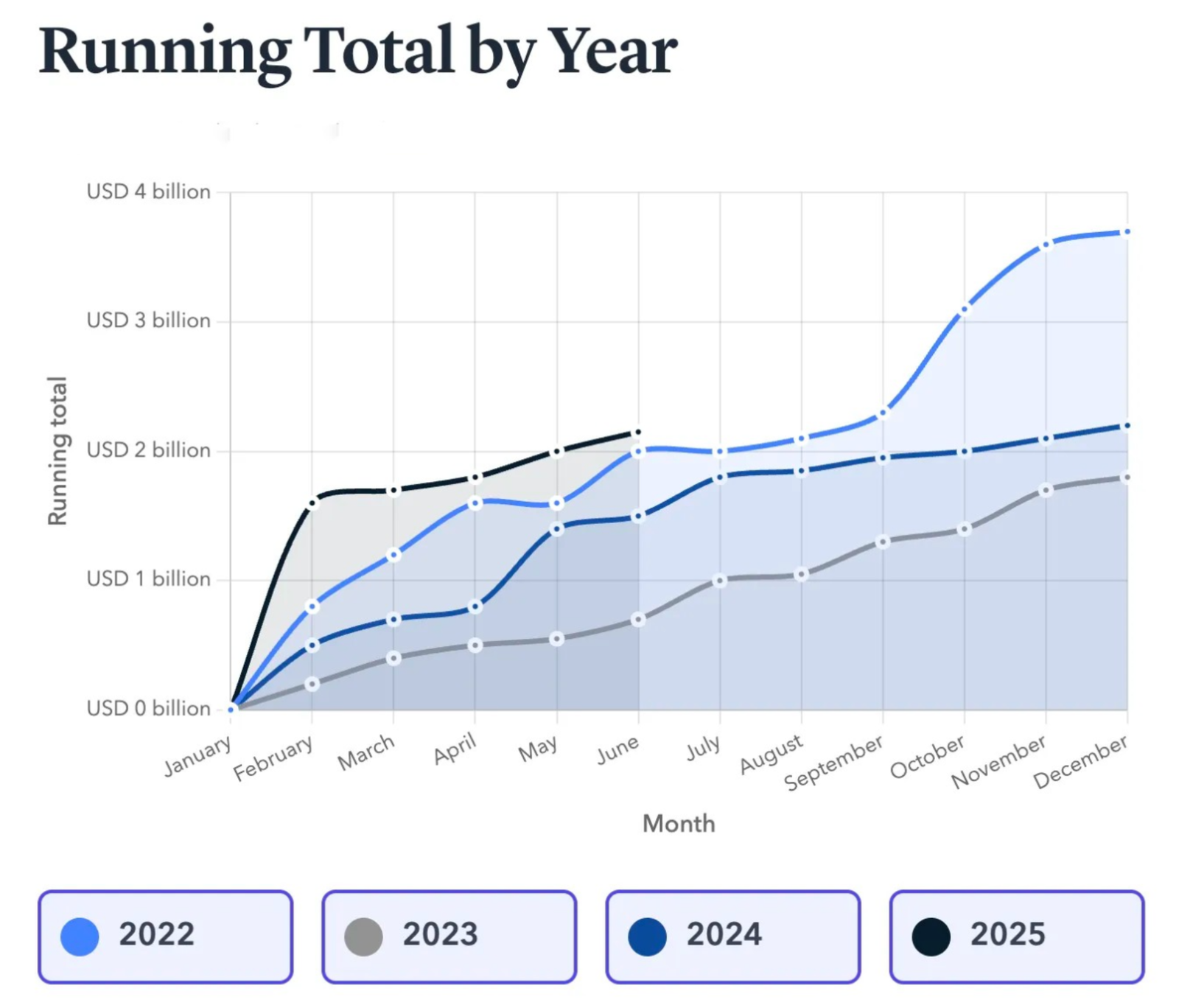
Without always-on, regulator-grade compliance the sector is on track to lose $2 billion+ each quarter.
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)

.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
| Compliance Failure | Why it matters | Hacken solutions that fix it |
|---|---|---|
| 🏦🙈 Hidden Reserves | Users & regulators need live proof assets ≥ liabilities. Real-time transparency prevents insolvency. |
 -- on-chain verification  -- continuous transparency scoring |
| 🔓 Loose Controls | Single-key compromises allow entire protocols to be drained. RBAC & multi-sig are critical. |
  -- crowdsourced vuln discovery |
| 📄 One-Time Checks | Code, keys & configs drift after launch; audits age out. Continuous monitoring required. |
 -- AI real-time code and operation security   |
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
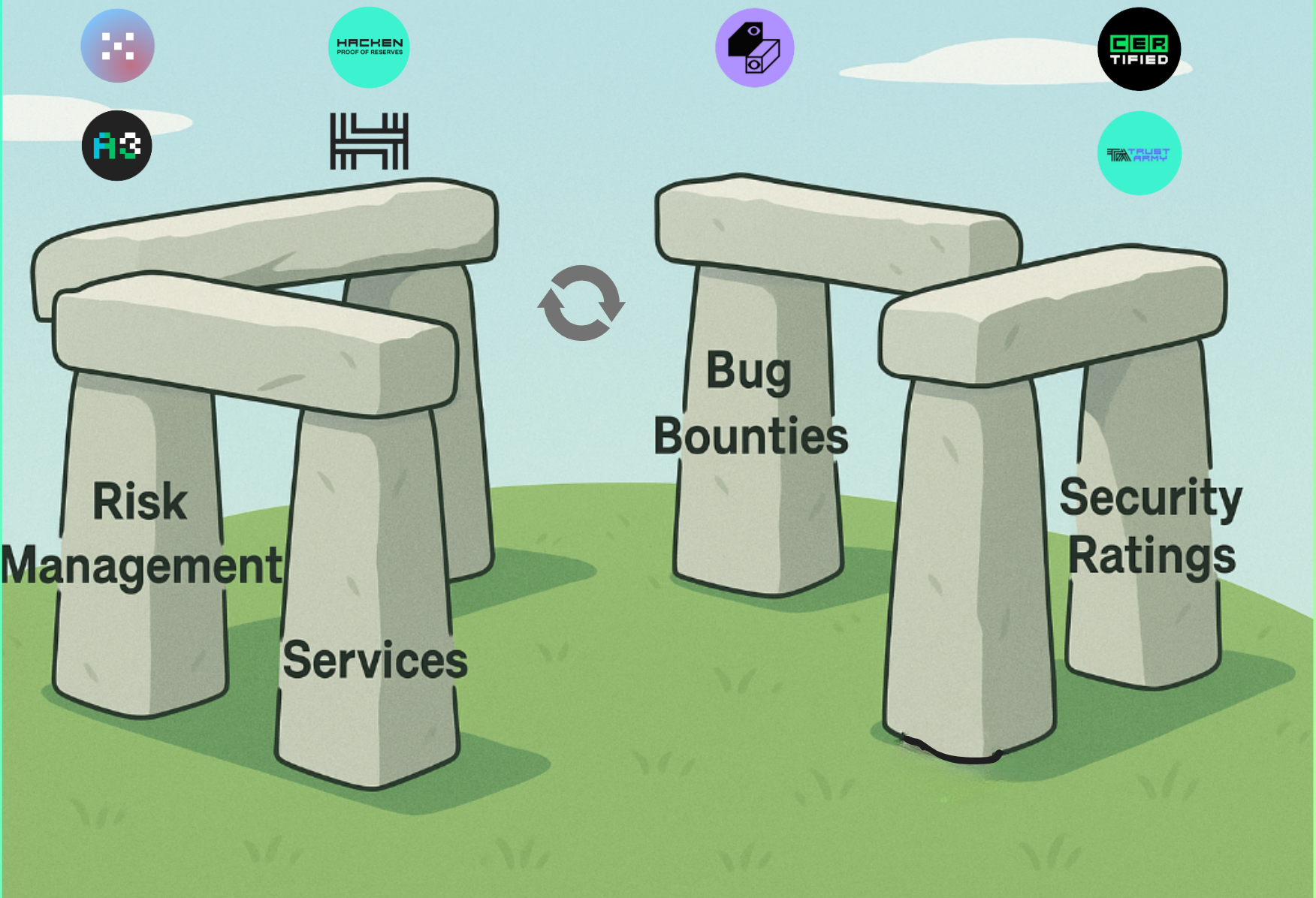
Hacken's ecosystem forms a continuous security loop:
• Services uncover vulnerabilities & compliance gaps → feed Bug-Bounty scopes & Risk dashboards.
• Bug Bounties crowd-source exploit discovery → sharpen future audits & enrich threat-intel for Extractor.
• Risk Management runs 24/7 checks → auto-triggers tasks for auditors and hunters.
• Security Ratings make all of this transparent -- rewarding strong security and pushing weaker teams back into the loop.
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
Direct control and consistent service delivery in core markets
Strategic partnerships for market expansion and localization
Revenue: Software licenses + 20% revenue sharing
Diverse federation potential with specialized expertise
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
| Vendor | Hacken | CertiK | Elliptic | Chainalysis | Hypernative | Chainalysis |
|---|---|---|---|---|---|---|
| Product | Extractor | SkyInsights | Elliptic | Chainalysis | Hypernative | Hexagate |
| Compliance Monitoring | ✓ | ✓ | ✓ | ✓ | ✕ | ✕ |
| AML Transaction Screening | ✓ | ✓ | ✓ | ✓ | ✕ | ✕ |
| Cross-Jurisdictional Compliance | ✓ | ✕ | ✓ | ✓ | ✕ | ✕ |
| Community Sentiment Monitoring | ✓ | ✓ | ✕ | ✕ | ✕ | ✕ |
| Real-Time Threat Detection | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Cross-Chain Security Monitoring | ✓ | ✕ | ✕ | ✕ | ✓ | ✓ |
| Risk Assessment and Scoring | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Dynamic Risk Scoring Based on External Events | ✓ | ✕ | ✕ | ✕ | ✓ | ✓ |
| Incident Response and Mitigation | ✓ | ✕ | ✕ | ✕ | ✓ | ✓ |
| Automated Risk Mitigation Actions | ✓ | ✕ | ✕ | ✕ | ✓ | ✓ |
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
According to Statista, the cybersecurity market is forecasted to reach 272 billion USD by 2029.
The current market growth phase (from 2023) is driven by institutional companies entering the digital asset space.
They allocate a higher share of their IT budgets (ca. 11%) to cybersecurity compared to the existing crypto companies (less than 5%).
This new market shift and the influx of traditional institutions present a new opportunity worth $4.5 billion in the Web3 cybersecurity market, with a forecasted growth rate (CAGR) of 44.9%.
Extractor is well-positioned to become the leading provider of SaaS infrastructure and services for the Web3 Security & Compliance market.
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
Extractor
CER.Live
HackenProof
AI Audit Automation
Core existing audit services (Smart Contract Audit, PenTest, L1, dApps)
Consulting (Tokenomics, Cybersecurity Strategy & Implementation, Post-Implementation Certifications and Education for Enterprises)
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
| Dyma Budorin | 53% |
| Fiat Lux Investments | 20% |
| Yev Broshevan | 5% |
| Andriy Matiukhin | 5% |
| Denys Ivanov | 2% |
| Mike Boxmining | 2% |
| Hacken community | 1.5% |
| Others | 1.5% |
| Employees equity options | 10% |
.svg?table=block&id=c6e17c2f-db1d-4761-abbe-0e4cb14548a4&spaceId=ed576f05-09f9-452f-8117-002ba1628f0b&userId=&cache=v2)
